AWS CLI
The AWS web console is great for learning about services and setting a few things up here and there, but it not practical when we're doing real cloud computing. Eventually we need to automate everything with code.
In the future, we will learn how to use advanced tools like terraform and palumi to automate our infrastructure. But for now, we will just get started with the AWS CLI, which is the simplest way to interact with AWS using code.
Install the AWS CLI
Once that's setup, you should be able to run the following command to confirm it's working:
Setup AWS Config
- session name: a name that will help you identify your aws organization,
account-name-sso - start URL: the custom url you setup in the previous section,
https://my-aws-demo.awsapps.com/start - region: any region is fine, I use
us-east-1because it's closest to me - scopes: just use the default
sso:account:access
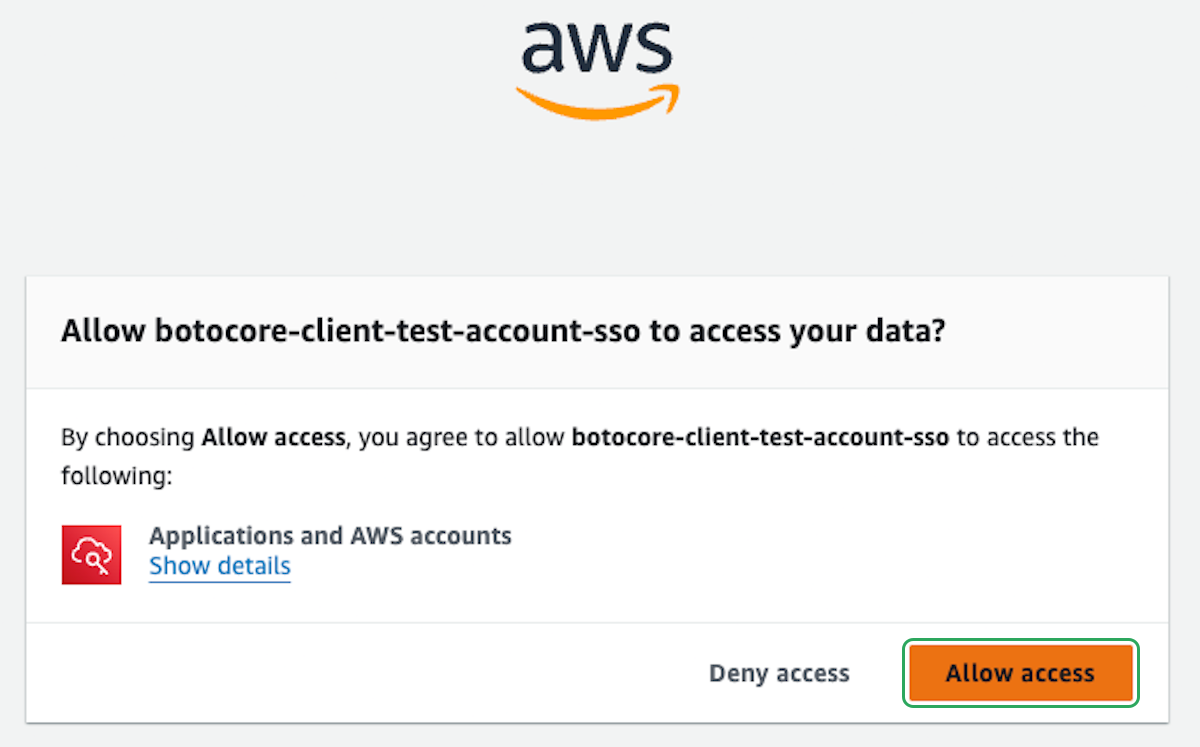
After you hit enter, you should see something like this in your terminal:
And you should be prompted to login with your browser.
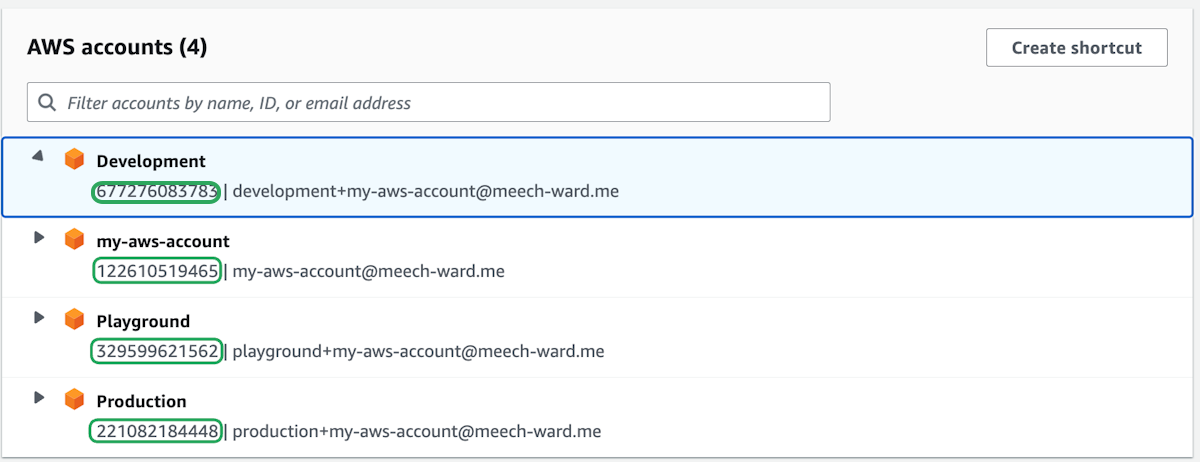
When that is successful, you should see something like this in your terminal:
It shows all four accounts that were setup, but only one of them can be selected at a time.
- CLI default client Region: use the same region that you used before
- CLI default output format: json is good
- CLI profile name: this is for the management account, so make it easy to identify that
The management account is now setup and ready to be used with the AWS CLI. Now we just need to do the exact same thing for the other three accounts. Or we can just copy and paste the profile we just created and change a few things.
Where the sso-session represents the SSO login for the entire AWS organization, and the profile represents one of the four AWS accounts.
So you will need four [profile ...] blocks, one for each account. But you will only need one [sso-session ...] block, which is the same for all accounts. Do not create any more [sso-session ...] blocks.
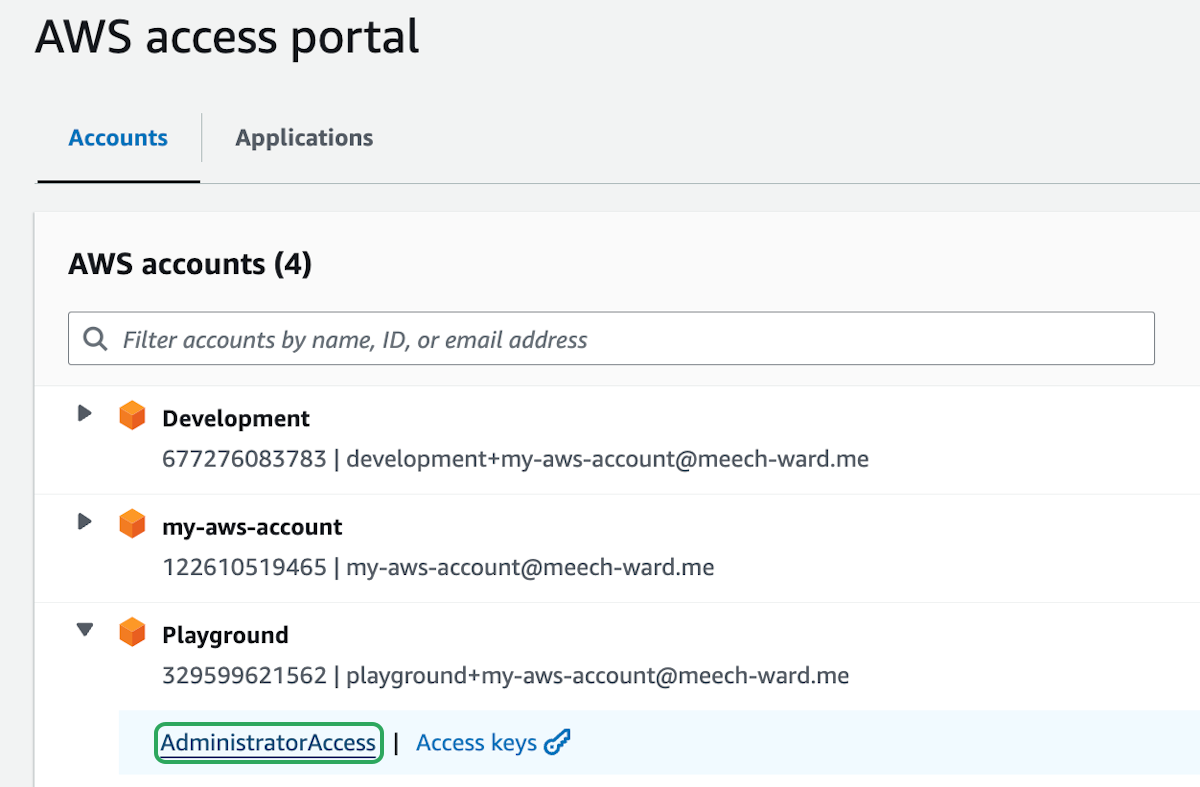
To find the account ids, you can enter your AWS URL in the browser. Each account has the id right below it.
Or you can use the AWS CLI and run the following command:
Make sure to use your management profile name.
Test Everything is Working
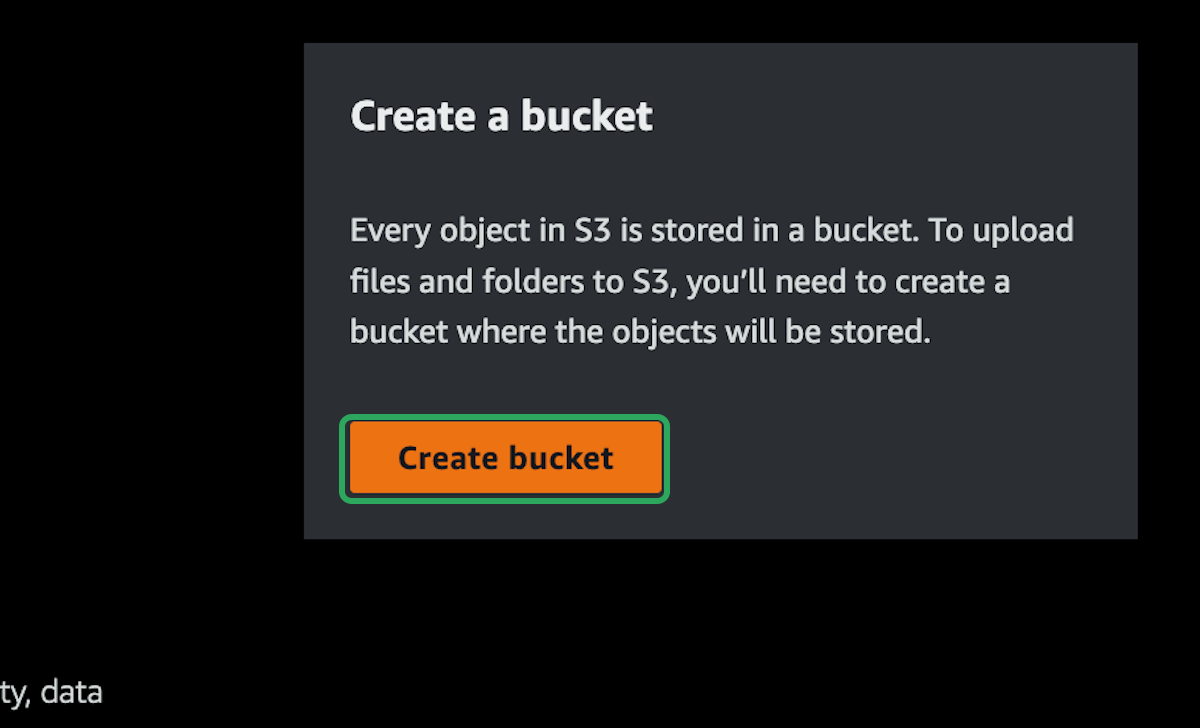
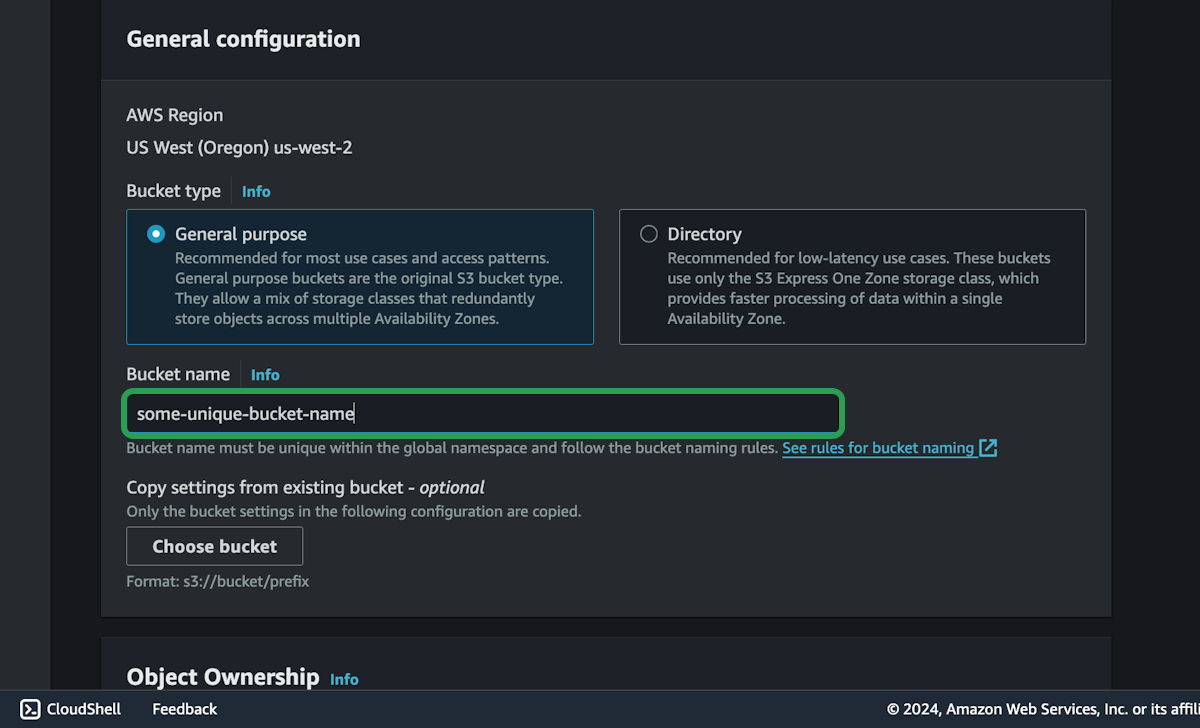
Let's quickly setup and teardown an S3 bucket, just to check everything is setup correctly.
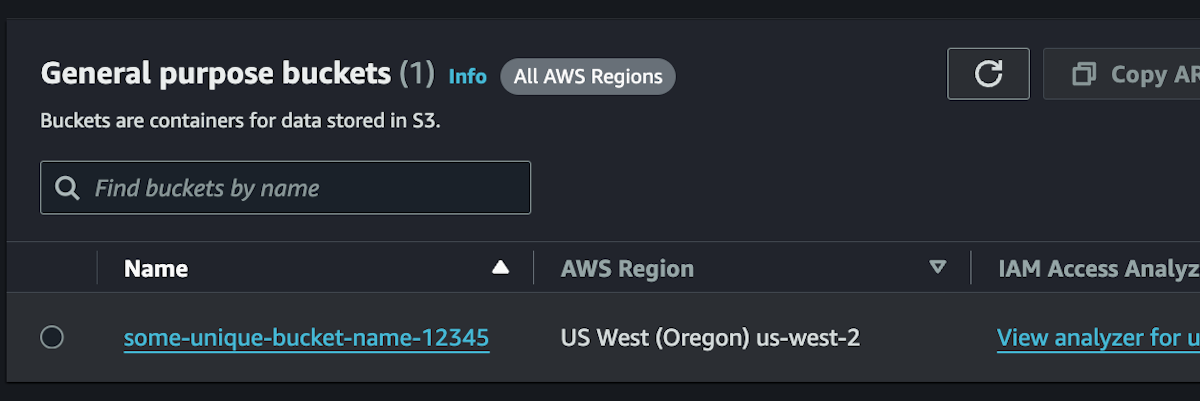
You should now see a single bucket created. You will need the bucket name and the bucket region to delete if from the cli.
To use the cli to delete the bucket, we need to first login to the playground account.
Refresh the page in the browser and you should see that the bucket has been deleted.
At this point, you are able to manage AWS infrastructure from the web or from the CLI. Now we're ready to start learning about how to use AWS.