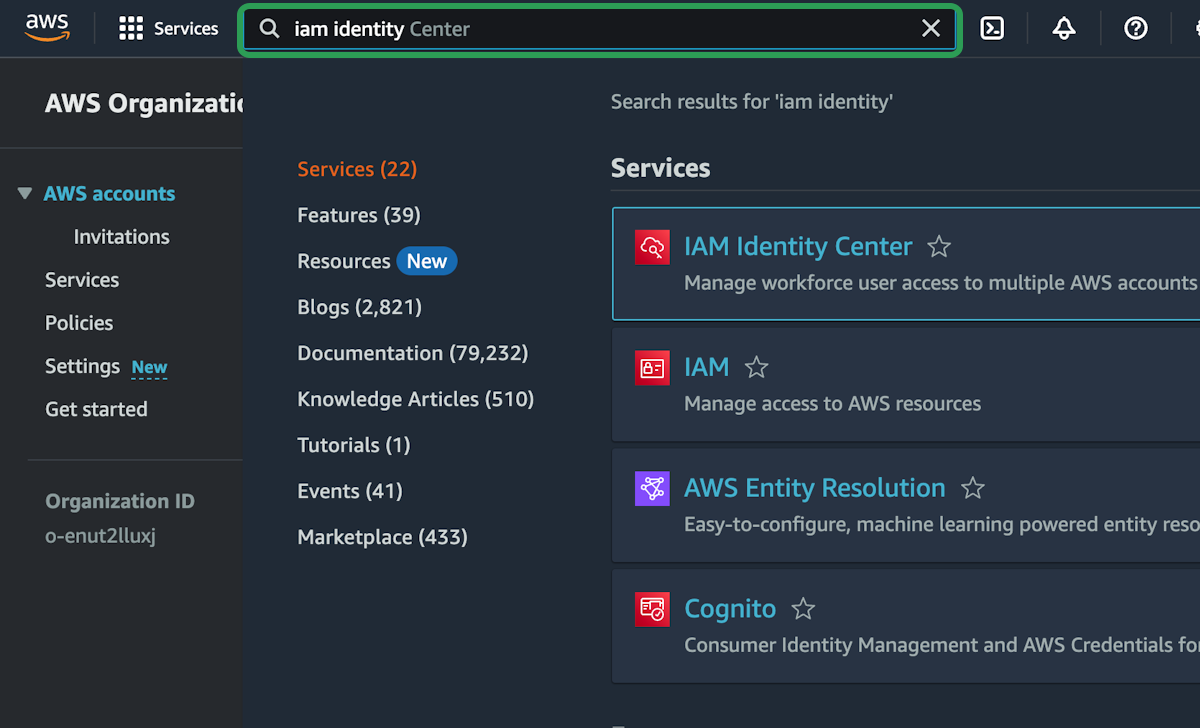
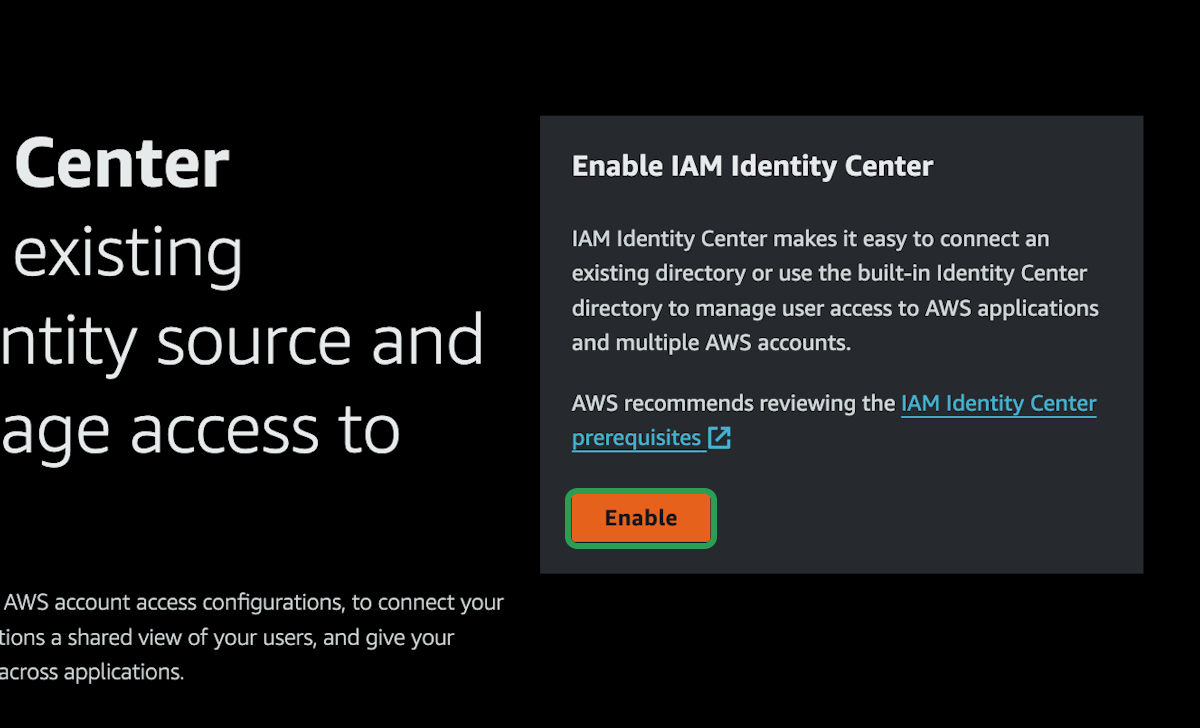
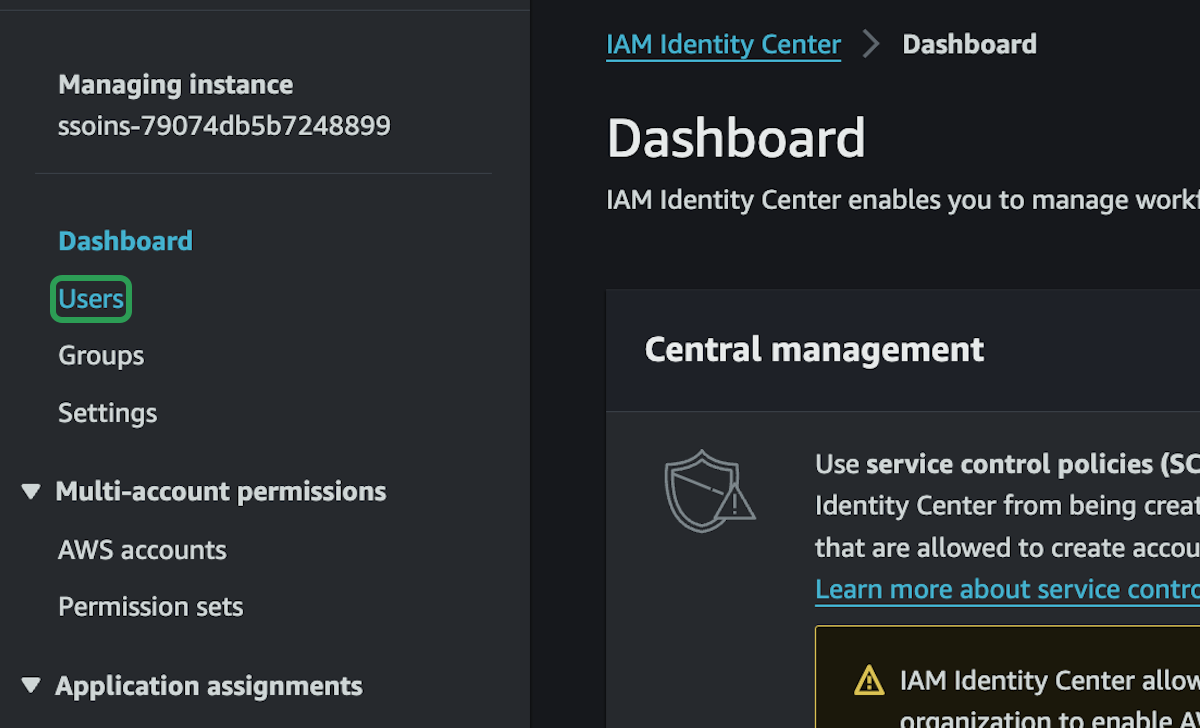
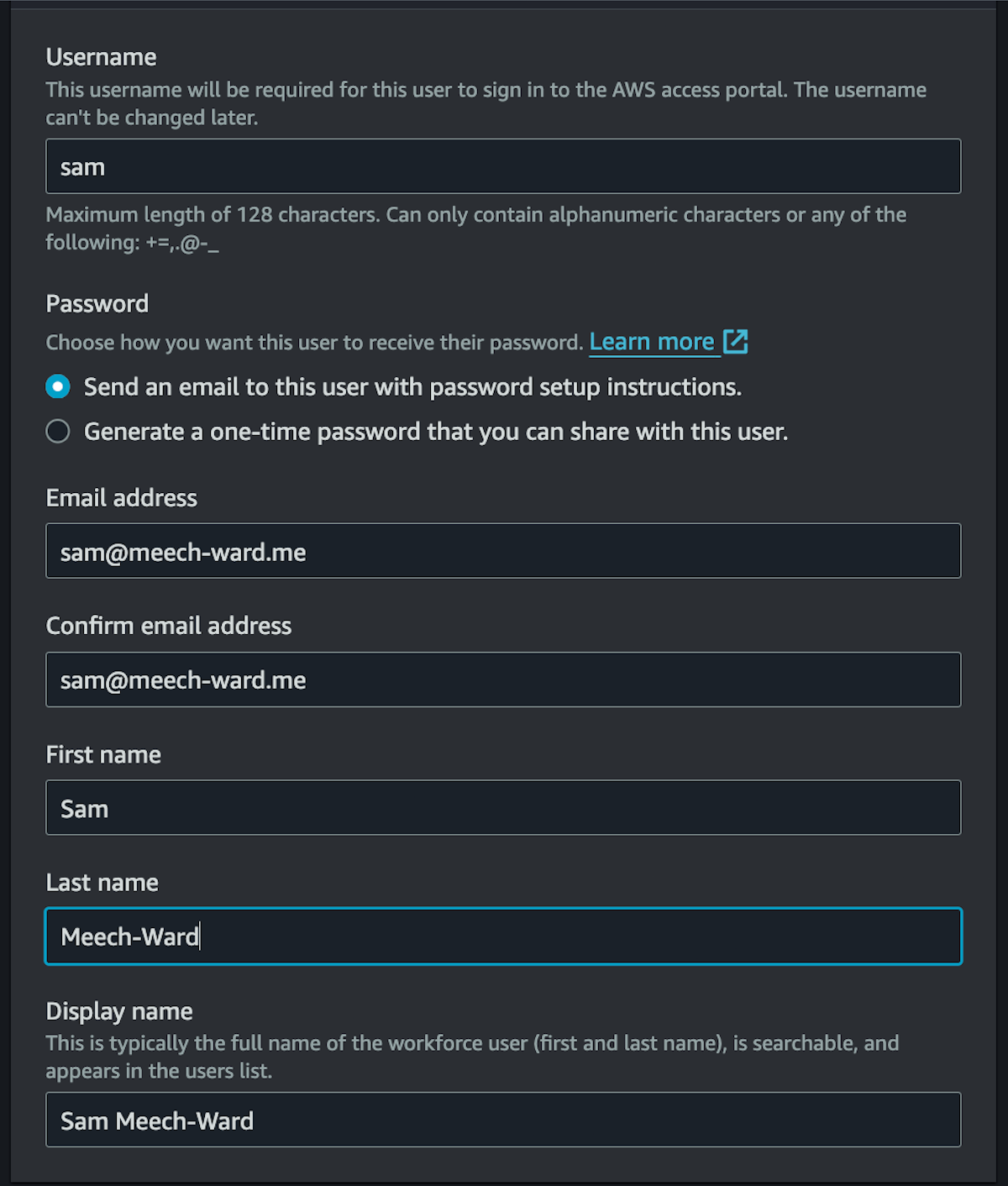
Add Admin User
We are currently logged into AWS with the root account which has unrestricted access to everything. If your login details were compromised, you would basically be SOL. So it's better to setup a different user with admin access that has a few more restrictions, has to re-authenticate more frequently, and can have it's access revoked if you suspect the details are ever compromised.
Groups are a great way of organizing users when you have a larger organization on AWS, but just for personal use, we don't need any groups.
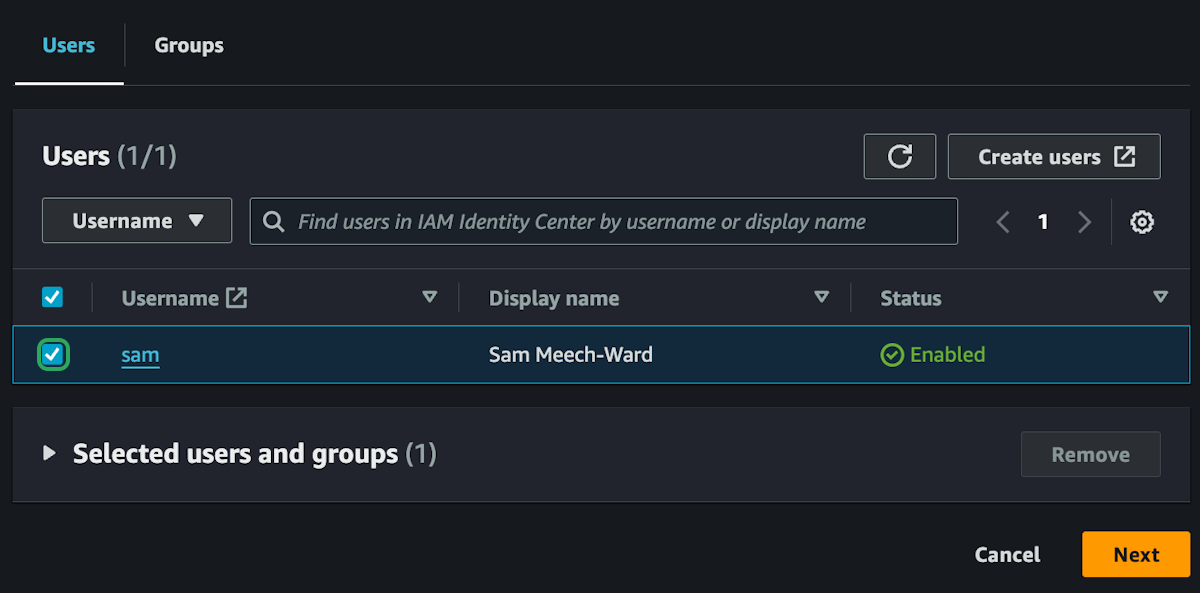
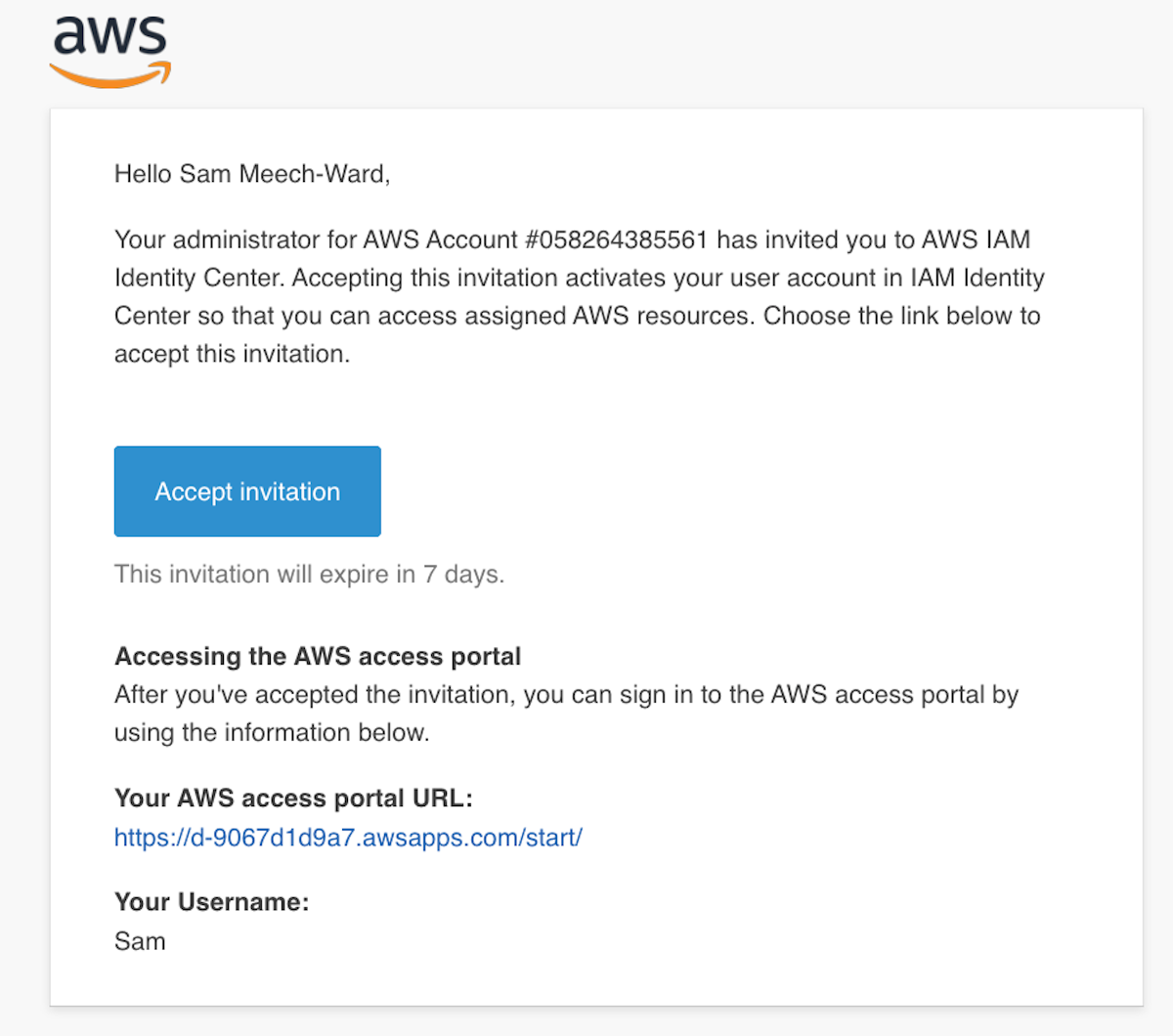
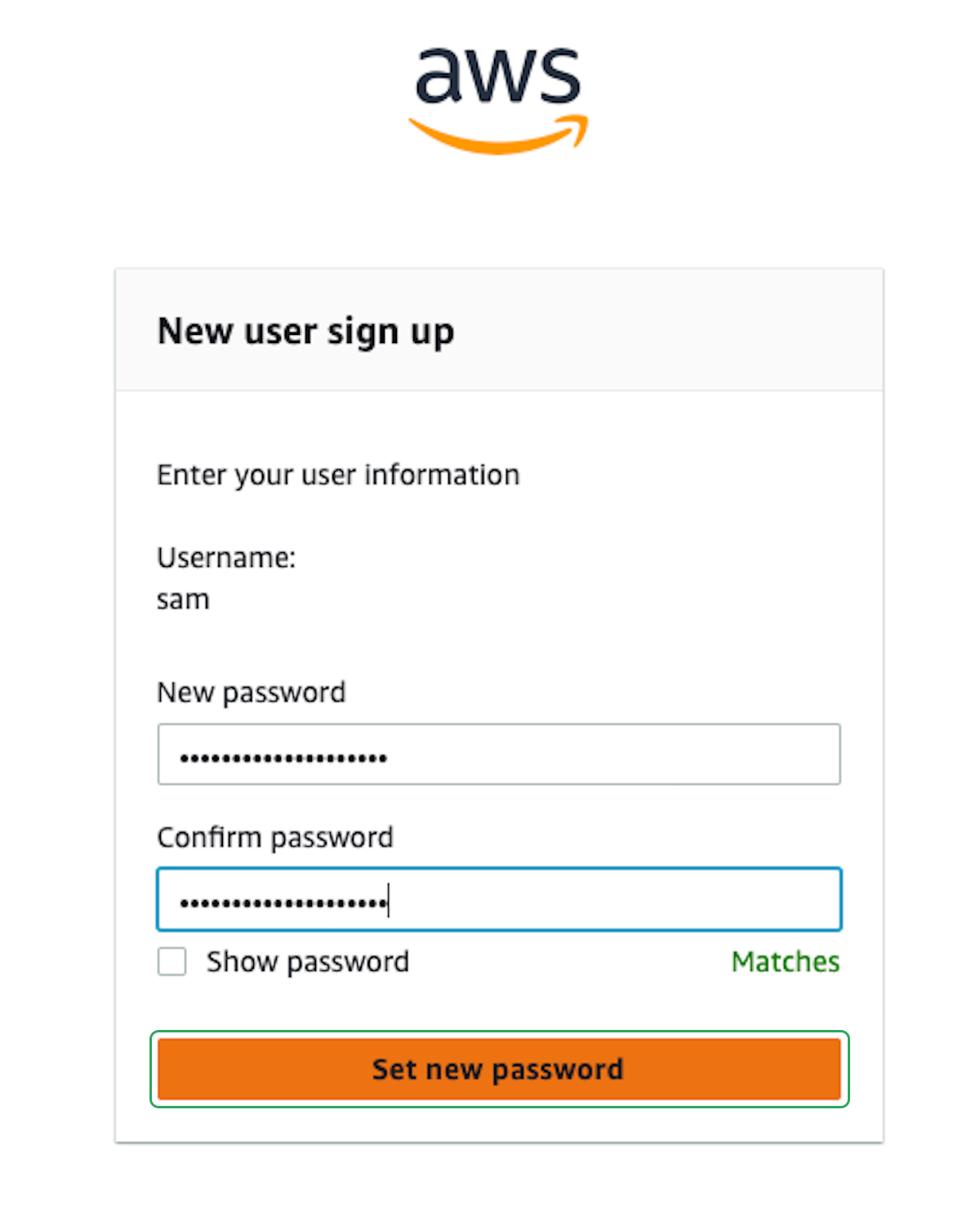
This will create the new user and send them an email to verify their account and setup their password. This new user account will be how you access everything in AWS.
Permissions
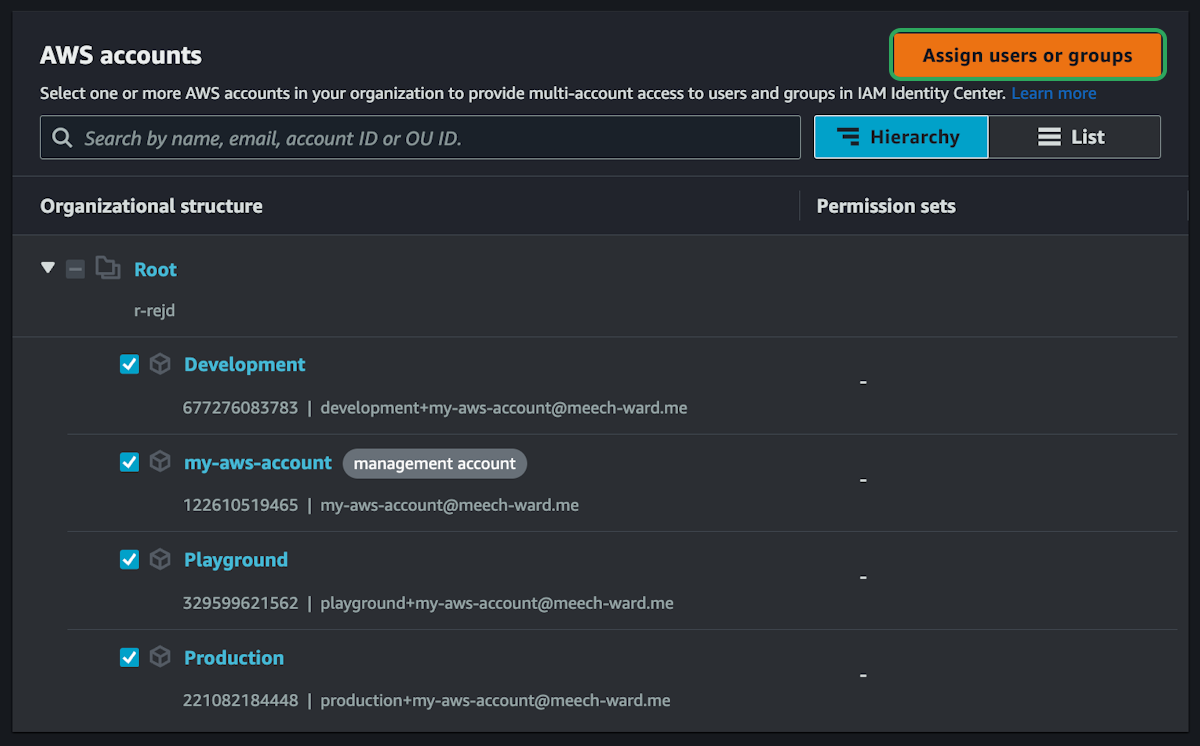
We have the user setup, but that user can't access anything. By default, everything in AWS is locked down and you need to be granted permission to do anything. So we now need to give the new user permission to do things in the accounts we created.
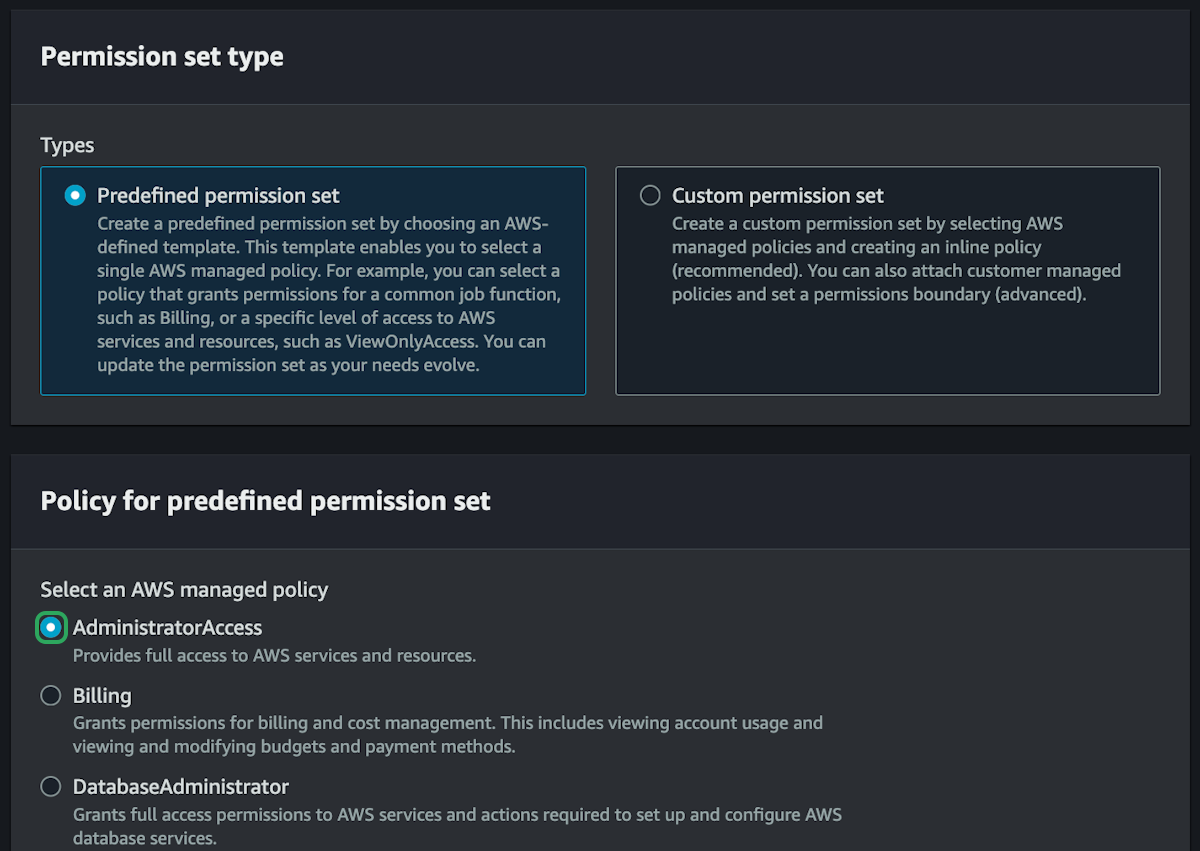
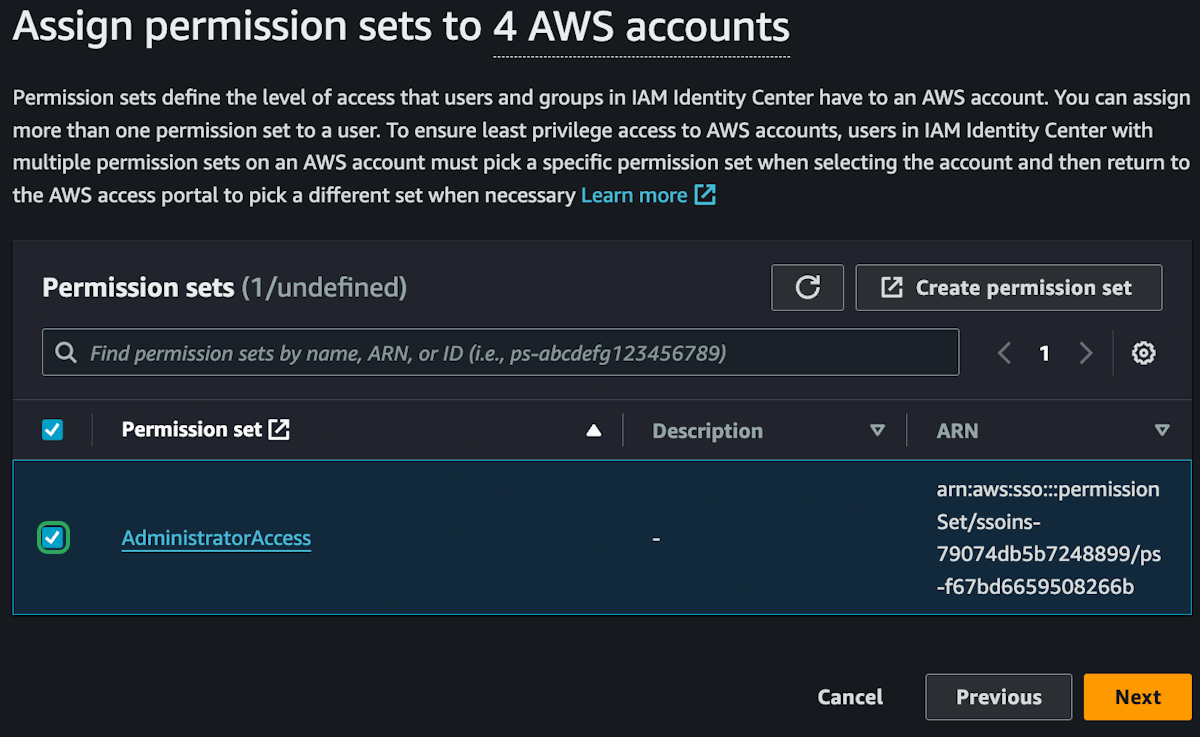
We can create custom permissions for users or use some predefined rules created by AWS. We are currently setting up the permissions for your own personal account, and you need AdministratorAccess so that you can do anything in your own AWS account. However, if you were creating users for other people like developers or business owners or DBAs, you would want to limit their access more.
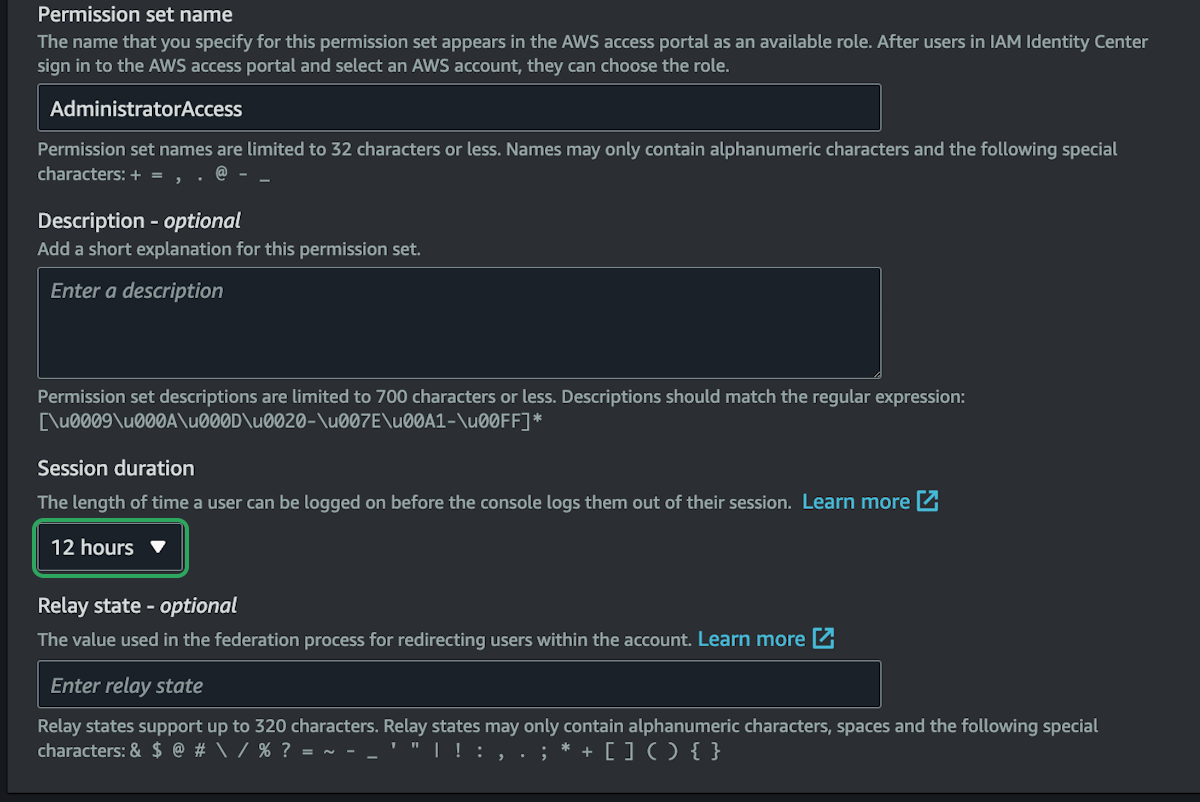
The session duration is how often you will need to re-login to your account. 12 hours is the current maximum amount of time. This is important to remember when using the CLI since you'll need to re-authenticate from the command line every 12 hours.
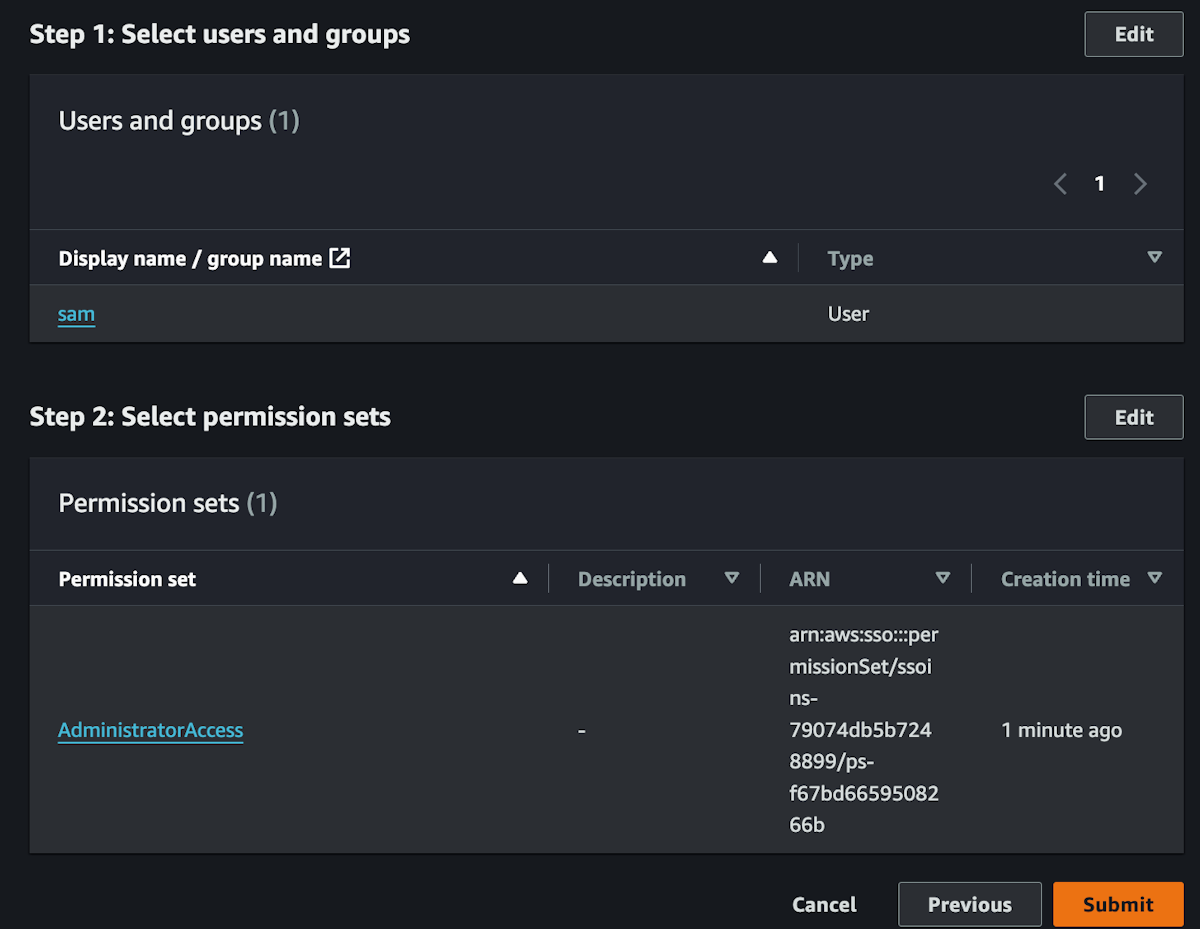
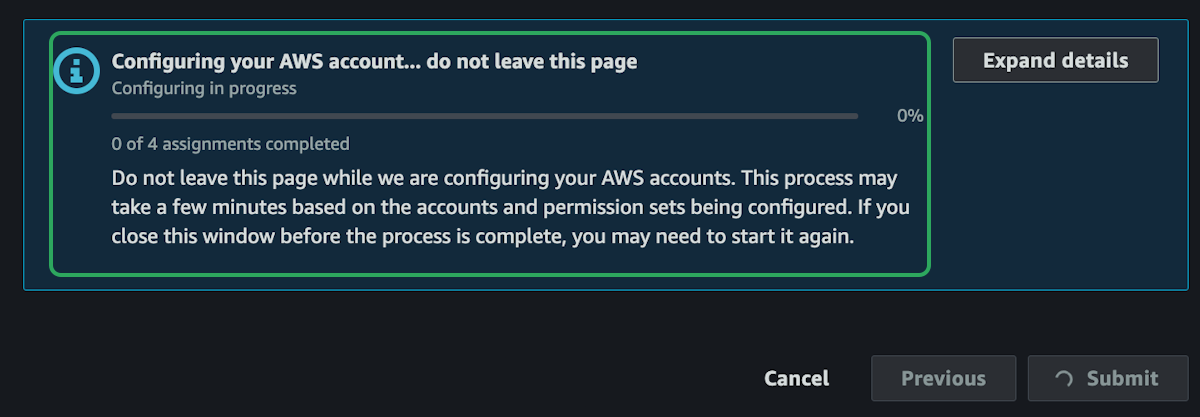
This will process giving the user admin permissions. Do not leave this page until it's complete.
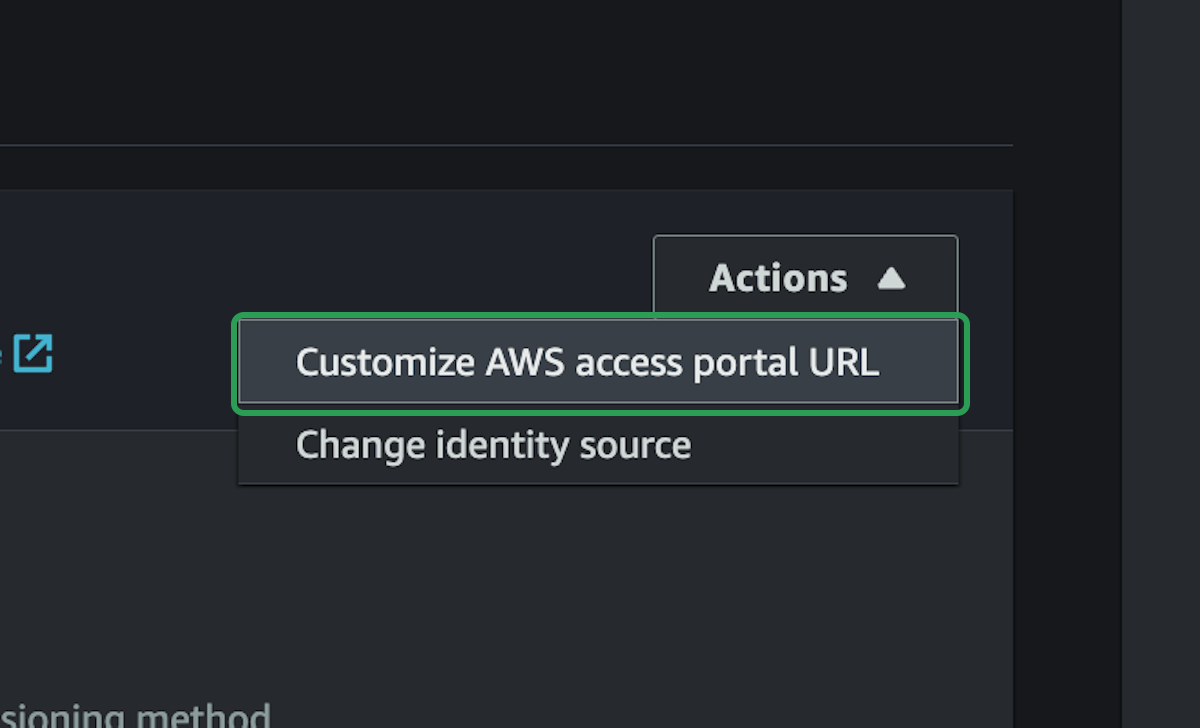
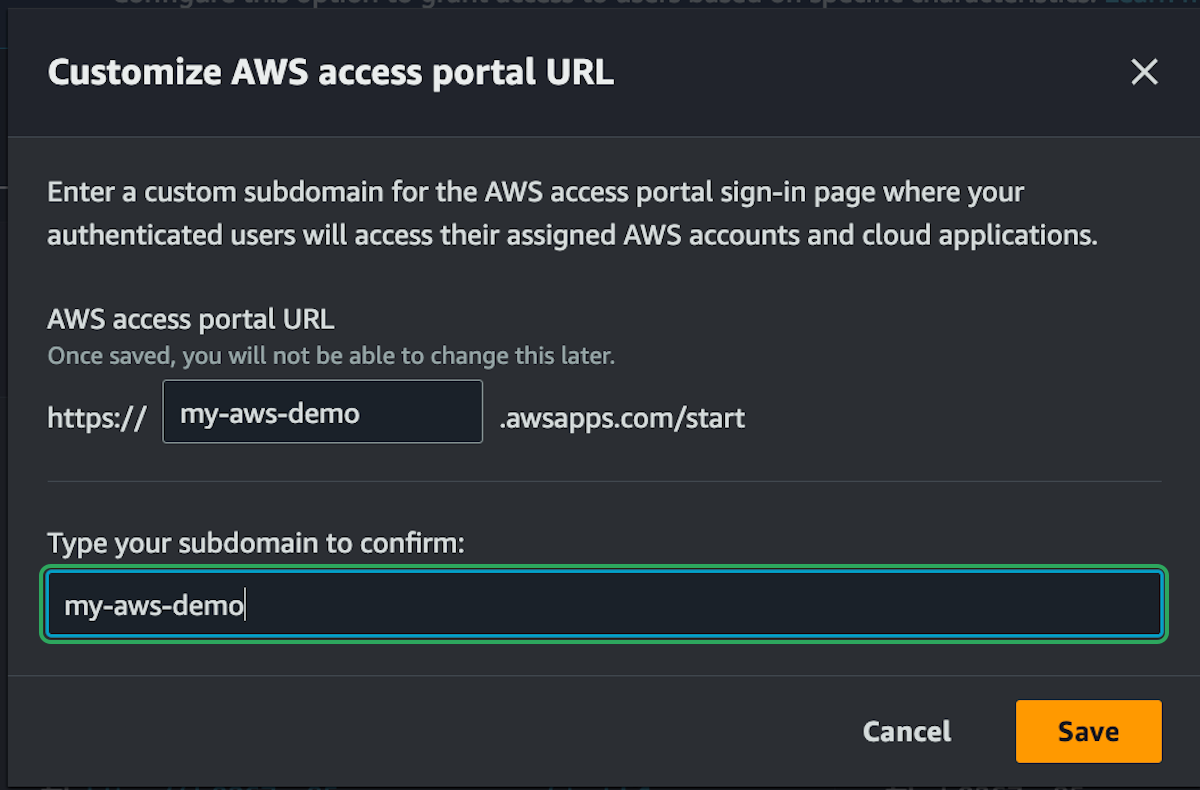
Custom URL
We're almost done, there's just one more thing that's nice to setup with our new accounts. A custom URL.
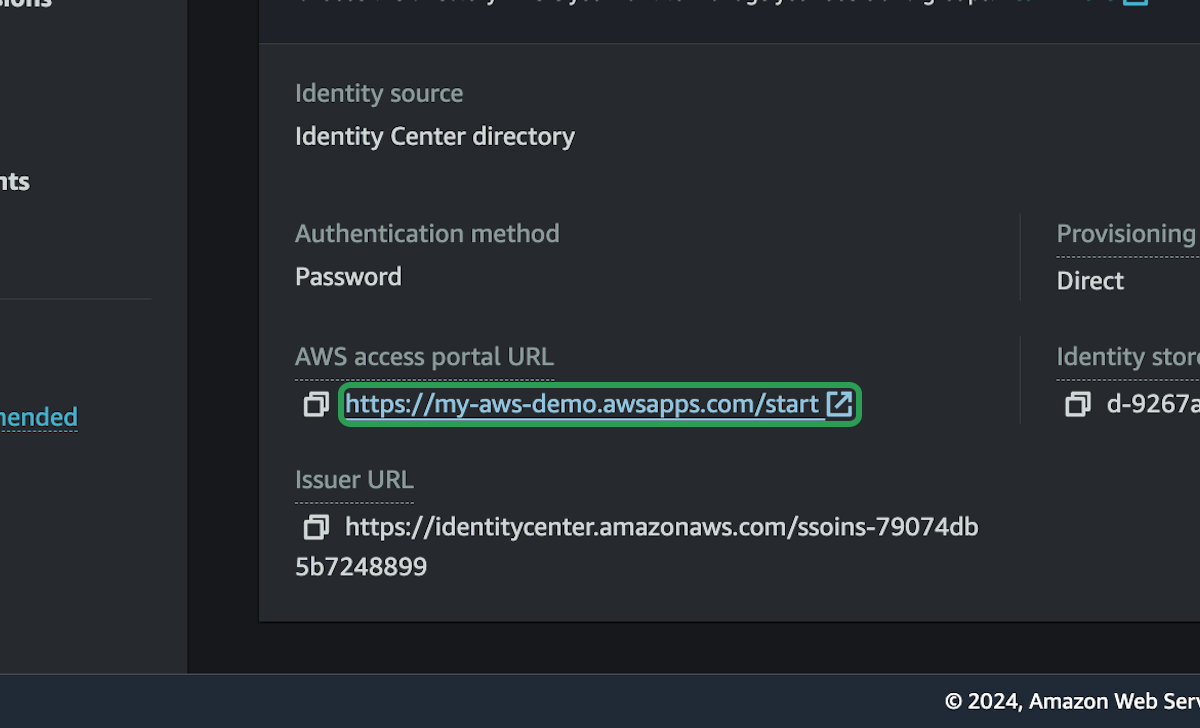
You will now be able to access you accounts with that custom URL.
IAM User
At this point, we're done using the root user account. If you need to delete your account in the future or create more users, you can login with this account. But for day-to-day use, we won't use the root account.
For the rest of this course, we will only be using the new user we just setup in IAM Identity Center.
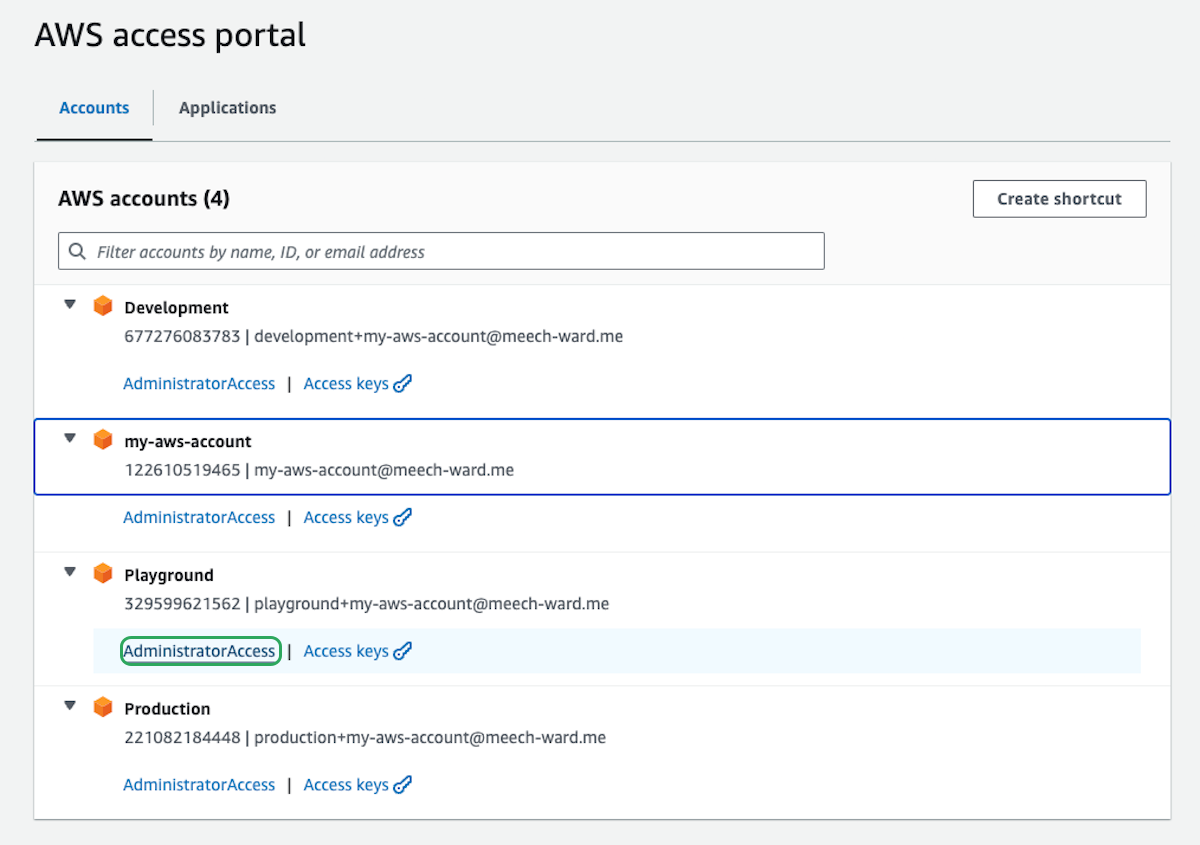
You should now be able to visit your custom AWS URL and see all the accounts you setup. This user can access any of those accounts with AdministratorAccess. If you click on AdministratorAccess under and account, you will be taken to that account. Feel free to go to Playground and take a look around.